Multiverse 2.357
paused to apply patches
What are VPNs? Virtual Private Networks are popular and a useful tool in your quest to guard your online security and privacy, as well as being an important tool for companies to allow remote access to their internal networks. Wikipedia defines them as follows, “A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network.”
VPNs have long been used in the enterprise to allow remote access to internal networks for remote workers, contractors, traveling workers, etc. In the corporate environment, VPNs allow remote users to access resources on internal networks. In the past decade, however, we’ve seen a surge in usage among privacy conscious individuals. It’s important to understand the security and privacy implications of VPNs, and to consider the criteria for choosing a VPN provider.
Using a VPN gives a user enhanced privacy in the form of protection from eavesdropping or logging of activity by the provider of network connectivity. For a typical user, this means their Internet Service Provider (ISP) will not know what websites, email servers, etc. they connect to, when they happen and for how long those connections last, or the contents of those communications.
VPNs give you protection from most Man-in-the-Middle (MITM) attacks. Establishing a VPN connection means setting up an encrypted communications channel with a server in the VPN provider’s network. After this is established, all communications between your device and the Internet is encrypted, preventing attackers from being able to read the contents.
When you establish an unencrypted session with a server on the Internet, an attacker between you and the destination can intercept, read, log or alter the contents of your communications. If you go to websites and setup secure communication with those web servers using TLS encryption, the Man-in-the-Middle (MITM) attacker can impersonate the destination server to you, and impersonate you to the server and neither will be able to tell.
This is called a MITM attack and it is a common and effective way to surveil people online. All traffic is encrypted, but the attacker decrypts your outgoing traffic, logs it, then encrypts it with what the destination server thinks is your private key. Incoming traffic similarly is unencrypted as it comes from the server and is intercepted. It’s logged, then encrypted with what your device thinks is the destination server’s private key. The attacker is decrypting, logging, then re-encrypting all traffic in both directions.
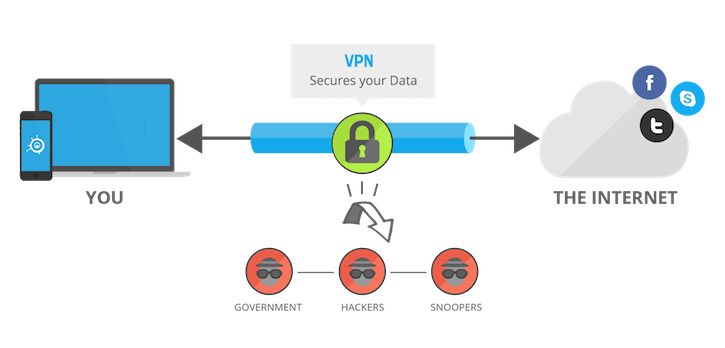
Using a VPN generally prevents this because the traffic is encrypted in the first place, before you negotiate an encrypted session with another server, so the attacker cannot see the traffic. The only possible MITM attack is an attack on your connection to the VPN when you initiate it. In other words, when you first establish a VPN connection the attacker intercepts this and pretends to be that VPN provider.
Mobile Devices
Users can use VPNs without a fixed endpoint, like when they’re accessing multiple WiFi access points. If you live in a place with free public Wi-fi you might have experienced this firsthand. Modern VPN software can deal with users moving between cellular carrier data networks, and public WiFi hotspots. Using VPNs on a mobile device gives users the same benefits they get from fixed locations; protection from MITM attacks, and privacy from the carrier network operator and any other intermediaries who might surveil or log the user’s network traffic.
On public Wi-fi networks the protection from MITM attacks is crucial. It is relatively easy to MITM attack other users on a local network using well known and documented attacks. Without a trusted VPN connection it is not safe to authenticate on any website or service while on a public WiFi network, so use of a VPN in this situation is considered vital.
From a privacy perspective, using a VPN service on mobile devices enables the user to protect all activity and contents of the traffic from the carrier network. The carrier will not know what endpoints are being connected to, when, for how long and the contents of those interactions.
Routers
For individuals concerned about online privacy, installing a VPN on a home router is a great strategy. Most devices used at home can connect to the Internet via a WiFi connection to the router, so if the router has established a connection to a VPN provider, all that traffic will be securely routed through the encrypted VPN connection. For home computing having a VPN client at the network level is an easy way to take care of all your networked devices.
The only exception is devices that connect via a cellular connection. If they’re portable devices, they should have a VPN client running on them for this reason and for reasons stated previously. Most mobile devices will also have the ability to use a Wi- fi connection instead of cellular, and can use the router’s VPN connection in this way, but might be configured to switch over to use cellular data if Wi-fi is not performing well.
Hopefully you finish reading this with a better understanding of Virtual Private Networks and their implications for security and privacy. Think about installing them on devices and at the network level to protect yourself. Business users will need to run their own VPN and tech-savvy indiciduals should consider it as well, but we’ll talk more about that in a future post. Next time however, we discuss choosing a commercial VPN provider for personal use in case you’re a little wary of running your own.