Multiverse 2.357
paused to apply patchesWelcome back to our series on conducting OSINT investigations on the Matrix platform. This is the fourth installment, so if you haven’t read the others you probably want to to go review them now. The first post was an introduction to the matrix platform itself – a high level description with an emphasis on items of interest to OSINT enthusiasts. After that we went through the Matrix data model in depth, exploring the available data for users, rooms and homeservers and where to find it. In the previous post, we talked about creating accounts, finding rooms and servers, and various tips and techniques.
We lamented that tools to help us automate routine tasks were few and far between, and in this post we’ll explore the RESTful API and review programming basics, as well as discussing libraries, frameworks and bots. Expect loads of links, because explaining things in more detail would result in an incredibly long post.
As mentioned earlier the Matrix protocol is built on HTTP and they have a nice RESTful API to use. You can see from the Matrix API documentation some non-destructive, publicly available “read” operations use HTTP GET requests. This includes useful OSINT interactions like fetching profile data, or asking a homeserver for metadata about a user. Other API calls use the standard POST, PUT and DELETE methods.
Read MoreWelcome to another in this series of OSINT investigations on Matrix. If you haven’t read it already, or for a quick introduction to the basics of the Matrix platform, please read the first article in this series. After that introduction we took a detailed look at the platform and it’s major components, how they interact, what data they expose, and how to find it – read it now if you want to learn about how data is organized on Matrix.
In this installment we’re going to look at creating accounts, and searching for rooms and homeservers. We’ll share a few tips about messages and other events, and discuss the sort of research you might find useful on this small but growing platform. Then we’ll wrap things up by looking at tools, bots and an introduction to building them. But that’s next time, let’s dive into today’s topic!
Read MoreIn the previous post we gave a high-level introduction to the Matrix platform, how it operates, what characteristics it has, and why it is interesting from an OSINT perspective. In the next post in this series, we’ll examine tools, tips and techniques useful to a researcher on this platform, followed by a closer look at building tools for Matrix researchers. Right now we’re going to see what useful data is available, where, and how to find it.
MATRIX DATA MODEL FOR OSINT
The major entities in Matrix are users and accounts, rooms, homeservers, and communities/spaces. In this post, we’ll dive into specifics: how they are related, what data is accessible with and without authentication, what data is optional, where to find specific data, and a bit about understanding the relationships of users, rooms, homeservers and their data.
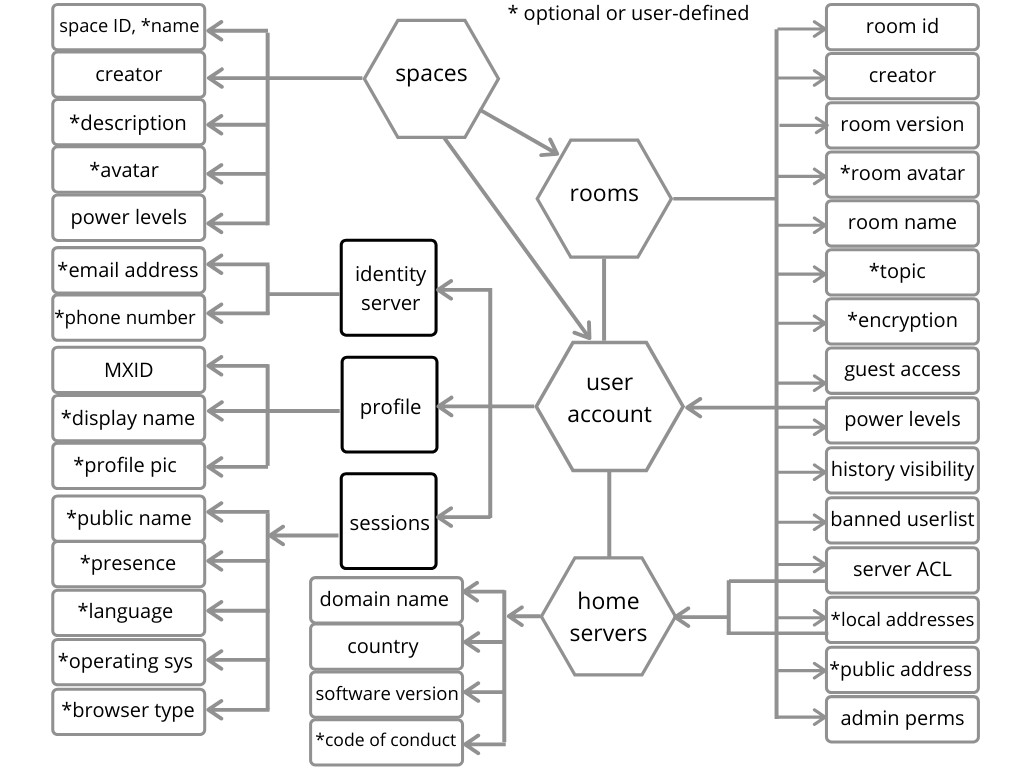
Here is my attempt to depict the relationship between those first-class entities in Matrix (above) and the available data we should look for that might be associated with each. I ran out of room thoughThis is surely not too useful without some explanation and some examples, so let’s dive in a bit deeper.
Read MoreENTER THE MATRIX

Matrix is a new-ish player in the messaging and group chat space, but the software ecosystem is stable and is becoming mature enough to be quite usable. My goal here is to introduce the platform and to then take a closer look at it from an open-source intelligence perspective, since this is less well understood than more mature and popular platforms out there.
This is the first post in a four part series, so stick around even if this introduction to the platform is too basic for you. I plan to get down in the weeds a bit in a couple of the later posts, including some programing examples.
Matrix is an open source, federated platform similar to XMPP. The Matrix API is pretty full featured and well-documented, as is the project in general. A great place to get started is reading their guides. This platform fits in a hybrid application category, being both a messenger that can be used for person-to-person communication, as well as for group chat for fairly large numbers of participants. Matrix has integrated support for voice and video chat as well but is a text-based messaging platform at its core. That does make comparisons difficult however. It is most similar to Telegram in terms of functionality, although they are quite different in most other ways.
Read More
I made three Bitcorns game challenges. These are challenges based on the fabulous Bitcoin token-based game called Bitcorns. This is the second of three challenges to get solved. Here is my description of the previous challenge. For those ambitious CTF types reading this, one still remains.
With each one solved, the winner gets to transfer out the contents of the farm. That’s because the challenge is to discover the seed phrase that unlocks the wallet at this address by inspecting the card and farm art for clues. Remember, these Bitcorn farms are just Bitcoin addresses that have Bitcorn game tokens. So at the farm address there was some Bitcoin (BTC) and some Bitcorn cards like the one shown on the right.
The “Yubicorn” card shown here and the farm are the sources for all clues. Having said that, both the card and the farm have their own pages in the game and all clues can be found in the images and text there. Let’s go through the clues that led to the winner getting
Read MoreBitcoin is hitting new all-time highs, and lots of people are suddenly interested. When they start asking general questions, I either explain what I can or point them to an “Intro to Bitcoin” podcast I did. Some questions require more elaborate answers – one of those topics is Coinjoin.

Coinjoin is an idea that goes way back, to at least 2014. The basic idea is to combine transaction inputs and outputs in order to obscure the source of those transactions. So instead of n number of users creating separate transactions, all n inputs and outputs are combined into a single transaction. If you look at the transaction detail, you’ll see a transaction where one input is no longer associated with a one set of inputs and outputs. Now those inputs are associated with the true outputs only with a certain probability.
Read MoreDedicated OSINT linux distros seem to be getting more popular now, bundled with tools for the job. Today I tried one from Trace Labs based on Kali linux. Kali linux is a debian-based distro loved by pentesters, and usually comes bundled with lots of tools for scanning, attacking, persisting and reporting.
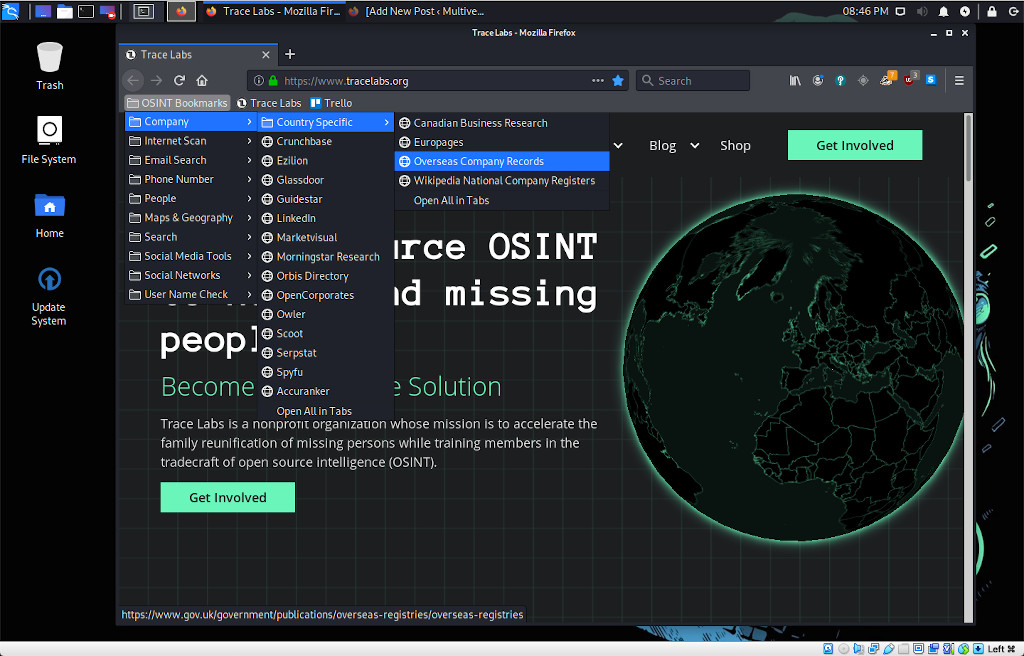
This distro has very few of the pentesting tools you normally expect with Kali. That makes sense, since the main area of overlap is reconnaisance, and there are few programs that you would normally expect to see in Kali.
Read MoreBokeh is a python module designed for plotting and graphing data in a web browser. I played around with this using Jupyter notebooks, Bokeh server scripts, and embedded in a Flask app.
I was able to generate a plot with a Bitcoin price ticker, which seems like a nice accomplishment for a starter project. I added some buttons to choose alternate cryptocurrencies to chart. It was a good experience, read on for the details.
Read More
Current “NISQ” quantum computers often produce errors when measurements are taken or gating operations are applied, and it is very costly in every sense of the term to deal with them. The ‘N’ in NISQ refers to “noisy; a reference to the fact that they are not capable of error correction.
High error rates are costly because you cannot copy a qubit during critical steps in the computational process. High error rates are also costly because error correction involves either redundancy in systems where there is a premium on qubits to begin with, or sending and receiving signals to and from the control systems into and out of the quantum processor hardware. Keep in mind also that these computations are often run thousands of times to give decisive results since those results are probabilistic in nature, and high error rates tend to increase the number of times these are run.
Read MoreThe makers of Autopsy and The Sleuth Kit forensic software are offering their Autopsy training course for a month for all those of us who are staying at home due to Covid-19. The course is from Basis Technology and the offer ends on May 15th. Go here for details: https://autopsy.com/support/training/covid-19-free-autopsy-training/
Autopsy is a general purpose toolkit for digital forensic investigations. It provides a GUI for their Sleth Kit software and other software, and is extensible via modules. The nice thing about Autopsy is the ability to automate the process of churning through and organizing large amounts of data like images from laptops and smartphones.
Read More
I recently recorded a podcast on this topic, and provided the obvious answer: because they will be able to do things that conventional computers can never do. I offered huge numbers to convey the potential, and analogies to illustrate the key differences, since the math required to really understand quantum computing is not compatible with audio podcasts.
The podcast, called What is quantum computing and why should we care? was published on HPR.
My strategy was to use an analogy I got from Talia Gershon from IBM. She talks about qubits by having the audience imagine spinning coins. Normal bits in conventional computers are just coins that are laying on a surface with either heads or tails facing up, that we can consider to be like 0 or 1. A quantum bit, or qubit, is a spinning coin. It’s not exactly a heads or a tails, but some combination of both of those possibilities.
The entry level explanation of quantum computing is that two spooky properties of quantum mechanics are used to do things current computers cannot. I mention those two quantum effects by name: superposition and entanglement, and proceed to use the spinning coins on a tabletop analogy to explain them.
Read MoreWelcome back for another look at the basics of quantum computer programming. We’re going to continue to use IBM’s excellent programming framework called Qiskit, and Jupyter notebooks to demonstrate with the usual disclaimer that you can code this without the notebook, and the same ideas can be realized in any quantum programming language. If you need a refresher on the basic math of quantum programming, we covered it in the previous two posts, although there is much more to it. If you want to review the entanglement program we wrote, first ran on a local simulator and then ran on a real quantum computer, feel free to review those as well, or maybe just review how to get started uing IBM Q.
The issue for this post is what can a quantum computer do that a conventional computer cannot? If Richard Feynman was the father of quantum computing, then David Deutsch was probably the uncle. Deutsch described a problem that takes multiple steps to solve on a classical computer and can be solved in a single step on a quantum computer. In this post we’ll describe the original version of the problem and show the quantum computer solution with hopefully a solid explanation.
Read More