Multiverse 2.357
paused to apply patches
Mimblewimble is the funny sounding and unconventional blockchain protocol that emphasizes scalability, privacy and fungeability. It is full of Harry Potter lore, cryptography and bright new ideas for cryptocurrency.
Due to the way mimblewimble is constructed, it’s best suited for comparisons to Bitcoin. If you need a quick refresher, consider giving my Intro to Bitcoin podcast a listen. Also, if you’re interested in learning more about the mimblewimble protocol you might want to listen to my Intro to Mimblewimble podcast on HPR as well.
Read MoreIn the previous post we started to explain how to understand quantum computing from a computer science perspective, even without knowing the underlying quantum mechanics. We did so by explaining that you can consider everything in terms of the math, and we began the process of explaining what happened in the quantum entanglement program we introduced in earlier posts.
It’s a useful technique to keep explaining things in a little more depth as we go down the rabbit hole. You may have noticed that I avoided qubits that are in a state of superposition in the last post, and chose to show the CNOT gate instead of the Hadamard gate. In fact I used |0⟩|1⟩ which are special cases where the qubits will collapse down to 0 and 1 with 100% probability. Qubits that have been put into a state of superposition will have a different probability distribution.
I won’t pretend to understand the physics of quantum mechanics, it baffles me to be honest. I only know the words that the physics people use to describe what happens. My limited understanding of quantum computing comes purely from a computer science perspective, so that’s all I can try to share.
A quantum bit, or qubit, is conceptually just the particle-wave duality of matter at very small scales. That is to say that a particle does not exist as a tiny billiard ball at a specific place, but rather has a probabilistic existence as a waveform. That’s the case until it is interacted with, otherwise known as being observed, which causes the quantum information to be lost and the probabilistic set of possible values to collapse into a single value.
I’m not going to try to explain why that is, or what is really happening here, since it’s beyond my understanding. Instead, I want to look at just the basic math that we need to understand how the qubits are affected by our gate operations. So let’s stick to the math, and explain exactly what happened in our quantum entanglement program used in our previous posts.
Read MoreQuantum Computing: Using IBM’s Online Computers
Friday , 29, November 2019 qiskit, quantum computingWe ran our quantum enatnglement program on a simulator in the previous post, so it’s pretty obvious what we need to do now. Qiskit is made for interacting with IBM’s quantum resources, so this is going to be easy. Let’s get started!
Qiskit has four main parts: Aer, Aqua, Terra, and Ignis. It is fashionable to name your quantum computing libraries and modules after the elemental forces it seems – others in the industry do it as well. The official qiskit documentation is the place to read up on this, but for our purposes let’s just point out that Aer has the simulator that we used in the previous post and handles management of the backends for us.
Read MoreQiskit is IBM’s open source, quantum computing environment for Python. We can use Qiskit to write programs to run in our local environment and run them on a simulator. We can also run them on IBM’s quantum computing resources via the IBM Q project. This currently includes six 5-qubit machines and one 14-qubit machine.
First we’ll need to install Qiskit, then create an account at the IBM Q site so that we can also run our programs on their quantum computers. You can skip this if you have a quantum computer of your own to use instead. We covered getting started with IBM Q Experience in the previous post. We used the quantum circuit builder to create two quantum registers and apply gates, then measure the result.
Read MoreIBM has quantum computers online and available for the general public to use for free. We’re going to look at interacting with them through the online interface, then we’ll dive in and take a look at writing and running programs using their Python framework called Qiskit. There are other great frameworks out there to use, and we’ll get to those, but this is a great place to start.
The first thing to do is to make yourself an account at the IBM Q site so that we can use their quantum computers. Usually people are eager to start playing around with these mysterious devices, but when you get a chance, explore the detailed documentation and learn what they have to offer.
We’re basically programming against a quantum computer at the assembly language level or just higher, in fact you might notice a reference to ‘qasm’ which stands for quantum assembly.
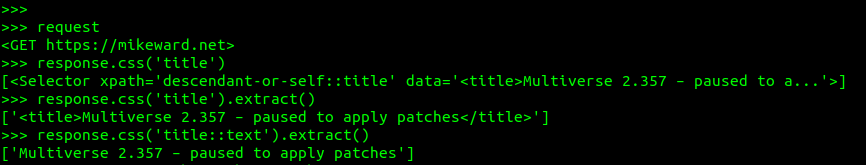
Read MoreScrapy is a scrappy little web scraper you can use to scrape web content using CSS or XPath selectors and even Regex. Using CSS selectors is probably the easiest for people who are familiar with the web, but the hardcore user can even mix-n-match.
We can open a shell, a familiar technique to Python programmers, in order to test our scraping before unleashing it on the world.$ scrapy shell https://mikeward.net
This opens a shell and the HTTP request and response are now available to us, as you can see below.
Health Information

Installing apps that “help” you with medical conditions can lead to privacy disasters. Your personal information gets shared with the world, and suddenly advertisements for your health situation follow you around the Internet. According to research firm Twinword, an estimated 83% of users searched online for health or medical information. If the average Internet user were to forget their medical issues, they could probably remember by spending an hour on the web watching advertisements.
Installing apps to help you with a pregnancy launches an avalanche of data sharing and advertising that almost defies belief. In the US there are laws that govern the use, sharing and storage of healthcare data, but it is a complex, nuanced issue.
Read MoreGetting Started
Install pass – use the package manager for your distro.
$ sudo apt install pass$ sudo yum install pass$ sudo pacman -S pass
Let’s try it out.
$ passError: password store is empty. Try "pass init".$ pass initUsage: pass init [--path=subfolder,-p subfolder] gpg-id...
We need a GPG key. Your distro should come with GNU Privacy Guard (GPG) installed already; if not install it now.
Read MoreI made a really difficult contest in the Bitcorns idle farming game. Actually I made three, and the one designed for hackers was recently solved, giving the winner the access to the private key. What this means in practical terms is that they could take the Bitcoin and the twenty five nice Counterparty assets at that address that I’m calling a farm. Cornfused? I’ll explain how this works, and in the process hopefully impress upon you just how insanely difficult this challenge really was.
The Cybercorn card itself is a token on the Bitcoin blockchain, only 32 were issued, it has clues hidden inside it, and it’s a card in the Bitcorns farming game. Not the reduced size one shown here mind you, the real one (shown below on this page) whose SHA256 hash was recorded upon issuance and used as part of one of the clues. That card image is an animated GIF, and when the corns fall down from the tree a clue is revealed on the empty branches.
Read MoreWhen people ask me about metadata and they’re not asking about a phone app, I default to saying exiftool because it’s fabulous and it’s the tool that I like. But it’s rarely a good answer for most people who want simpler things. So I looked at MAT2, the successor to Metadata Anonymisation Toolkit (MAT).
It is a python script with only a couple of options, but supports a LOT of file formats, including most office document formats, image formats, and many audio and video formats.
Read MorePaper wallets are the safest way to store cryptocurrency.
That’s a generalization, and of course the “safest” way to store tokens varies depending both upon your circumstances and what you consider safe. But generally peaking, depite numerous debates that will undoubtedly continue, the fact remains this is the most secure method for storing cryptocurrencies. That’s because you minimize the electronic attack surface, reducing the defense to the physical realm.
There are dangers and pitfalls with paper wallets to be fair, but they are entirely avoidable. That’s what this post is all about – debunking the popular notion that paper wallets are a good choice in theory, but not in practice! Let’s see how it goes, and please – to the makers of hardware wallets, I use your products and love them, it’s not personal.
Read More