Multiverse 2.357
paused to apply patchesI made a really difficult contest in the Bitcorns idle farming game. Actually I made three, and the one designed for hackers was recently solved, giving the winner the access to the private key. What this means in practical terms is that they could take the Bitcoin and the twenty five nice Counterparty assets at that address that I’m calling a farm. Cornfused? I’ll explain how this works, and in the process hopefully impress upon you just how insanely difficult this challenge really was.
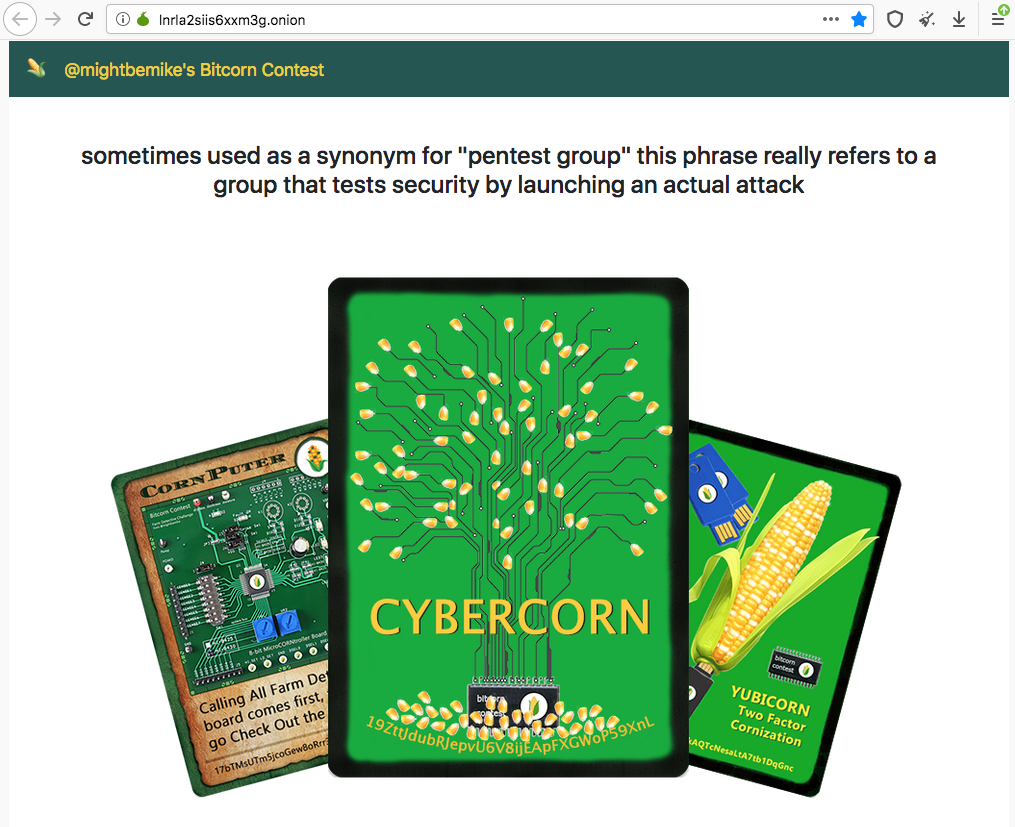
The Cybercorn card itself is a token on the Bitcoin blockchain, only 32 were issued, it has clues hidden inside it, and it’s a card in the Bitcorns farming game. Not the reduced size one shown here mind you, the real one (shown below on this page) whose SHA256 hash was recorded upon issuance and used as part of one of the clues. That card image is an animated GIF, and when the corns fall down from the tree a clue is revealed on the empty branches.
The other main part of this is the farm itself that goes with this card. The farm page has a large image, a title and description, geographic location, a collection of cards (tokens) and more. People are searching for 12 words that make up a seed phrase, and they can be hidden in any of the editable parts of this farm page. Finally somebody actually found the phrase, took the prizes and now I can disclose how I hid the clues!
The first two clue words were separate, the rest of them came in pairs. Words one and two were both hidden in images. On the game’s card page, there is a link labeled, “Dan’s Vision” which links to a higher resolution version of a card, if available. In this case a high res version does exist, but with an extra frame inserted into the animation with the number 1 and the first clue word. So far not bad, right?
If you’ll notice, in the card animation the digits 00101010 appear at the top after the corn kernels fall. This is referred to in a comment added to the EXIF data of the farm image shown below. The comment says, “stego pass lives in the treetop,” and implies that this string is used to decrypt a seed word hidden somewhere. That somewhere turns out to be the farm image above, only the password to decrypt is actually “42” which is the decimal representation. This second word was obviously a bit tougher than the first.

The third and fourth words come together as a pair, just like all of the remaining words do. These were probably a bit tricker than the previous word, but also hidden using steganography. Remember that hi res version of the card labeled, “Dan’s Vision?” Well the EXIF data for that file has another comment field added that points to a IPFS hash – a link. Following this link will give the clue hunter a text file with a short message:
Inside this text file is hidden the clue – words three and four of the seed phrase. Many people do not realize, but you can hide text inside text files using a steganographic technique called SNOW. This method encodes ASCII characters in the whitespace at the end of lines and on blank lines. Rather than check all the visible words, success comes from realizing that the clue is hidden in the file and not visible. It’s worth mentioning that there is an official list of valid words to check guesses against, and this was one of the many helpful and necessary hints given in the telegram chat room.
Now the next clue also employed steganography to hide words five and six. But it was definitely not a walk in the park for anyone who completed the earlier ones. This clue was hidden in the card image itself. The EXIF data contained the clue: “unlock a couple words from this file? use falling kernels as your pass” which is a tough clue. If the clue seeker realizes that unlocking a clue from this file refers to steganography, then they might realize the falling kernels part refers to a password that is needed.

The actual password here is the number of kernels that fall from the tree in this animation! That password is used to decrypt the words hidden in this card image file using a little known program called gifshuffle. This 2003 software encodes data into the color table by arranging the colors in the GIF palette in a certain order that represents that message. There is no need to have any idea how the program does what it does, but this program is not widely used, and unlikely to be tried by the contest sleuth. Fun times, eh?
The next two words were hidden in plain sight using the text on the farm page that the user can edit. There is a farm name and a description, and I hid the words in the following description: “Cyber renegades and corn kings, protect all silicon soil.” The seed phrase words here are “crack pass” taken from the first letters of each word and suggesting password cracking.
For words nine and ten, I used a bit of redirection. The asset description for Counterparty assets is limited in length, so people who create assets typically put a hash of the asset image there, or link to a JSON file with room for a more detailed description. That’s exactly what I did when I created the CYBERCORN card/token. The JSON file contained a few fields like the SHA256 hash, and one with the url for the real clue:
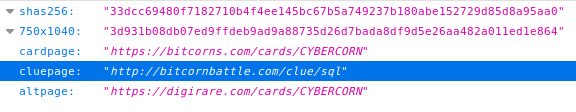
The real clue came in the form of an image that suggests the two words well known to database programmers. In the relational world foreign keys are used to preserve relations without needing huge, inefficent tables. A common operation is illustrated below, called an “inner join.”
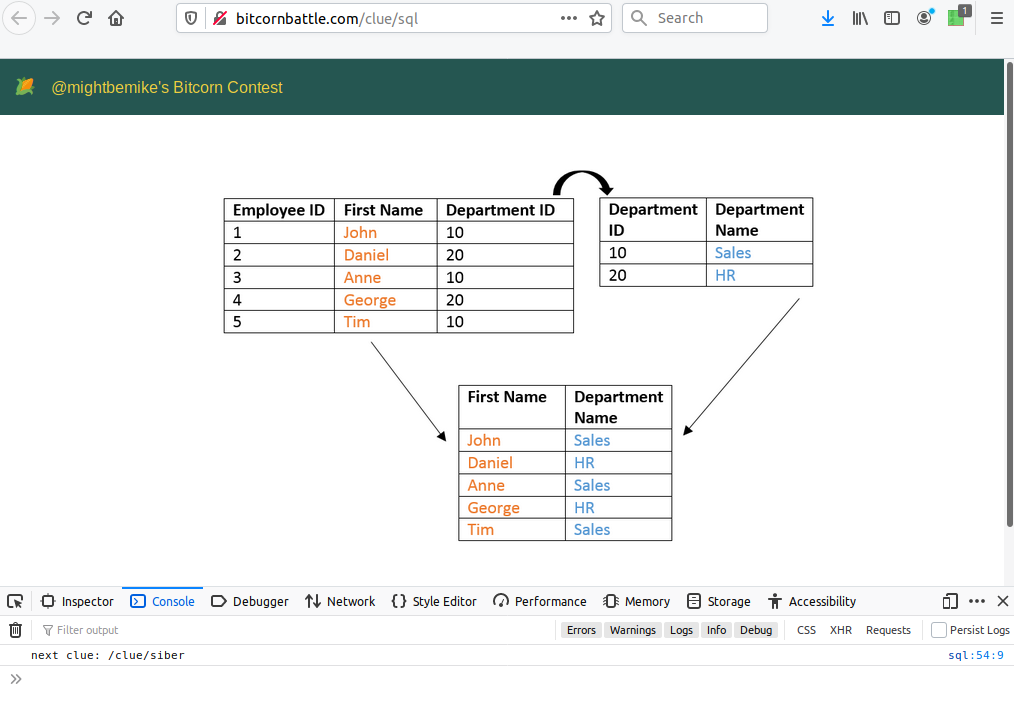
You might notice in the image above I’ve got the console open, and it shows the location for the next clue. It’s a relative url that redirects the user to a onion site with another two words for the seed phrase. The onion site gave what should have been an easy clue, since this contest was designed for hackers at I mentioned at the outset.
Upon solving this puzzle the winner logged into the wallet using the entire seed phrase and, using the 0.001256 BTC in there, transferred the tokens/cards out to a safe address. The other two farm + card puzzles remain unsolved, so I’m not going to say anything about them except that one is tailored to graphic artists and the other is for puzzle solvers who are interested in blockchains as well.
