Multiverse 2.357
paused to apply patches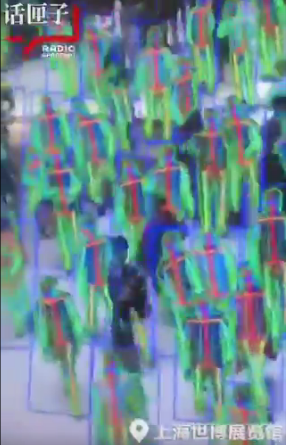
China is pioneering efforts to track and surveil their citizens using AI systems with data from facial recognition systems paired with other tracking technologies. Body movement or gait analysis technology has been deployed already in Shanghai and Beijing, and perfectly complements facial recognition technology for this purpose.
One company, Watrix, has software that can identify people based on physical characteristics from up to 50 meters away, whereas facial recognition technologies require a relatively close view of a person’s face. However once scanned at close range, an identified person can be tracked at a distance using gait recognition software from pretty much any system of cameras.
Read More
The Simple Mail Transfer Protocol (SMTP) has survived to this day due to widespread use, enabling us to send email messages quickly to people all over the planet. Yet email remains a sore spot for privacy advocates and a nightmare for security professionals. Email was the first real application on the Internet, and remained the most popular app even after the web became popular in the 1990s.
In the 1970s when the Internet was still being developed, people read and sent email by logging in to a central computer on a console and used a text-based email program. This basic technique of sending text messages and reading them using simple email programs continued to be the primary method of communicating online through the 1990s. But now, with yearly email messages sent somewhere on the order of one hundred trillion , it has grown into an unrecognizable beast.
Read MoreGoogle filed a patent application for “Smart-home automation system that suggests or automatically implements selected household policies based on sensed observations”. This is a futuristic look at automated systems that monitor “temperature, humidity, lighting, water, power usage, sound signals, ultrasound signals, radio-frequency, other electromagnetic signals or fields, GPS, proximity, motion, light signals, fire, smoke, other gas, etc.”
Google’s smart home vision includes modules to allow setting household policies that are marketed as controls aimed at empowering parents to limit children’s activities; e.g. no television before doing homework. This is accomplished via a household manager module, that infers everything from occupants’ activities to their emotional states.
Read MoreWelcome back to another Python programming post. This is a followup to my previous posts about using scapy – that versatile network traffic utility. We went through the basics of creating custom packets, using the basic scapy commands, and then looking at how to build a simple DNS query program using scapy. Feel free to go back and look at those if you missed them – I’m learning as I go, so I tried to be thorough.
In this post we’ll take a quick look at a couple of useful but completely different python utilties called Dshell and Impacket. They’re both unfortunately written for Python2.x, but they are both powerful tools that I’ve recently played around with and they’re worth knowing about. Let’s start with Dshell.
Read More
What will facial recognition systems look like in five or ten years? Welcome to the first post in this whole biometrics series to consist entirely of idle speculation! After building up a basic description of the status quo, it’s time to extrapolate forward based on nothing more than intuition.
Some trends are obvious: increasing resolution of cameras, continued miniaturization of cameras, improvement of facial matching algorithms, the rise of machine learning (ML) systems to manage these tasks at scale, the explosion of affordable satellites, increasing availability of personal biometric data due to breaches from governments that they just cannot resist collecting and warehousing, and development of complementary technologies such as gait recognition.
Read More
Interest in steganography is increasing. In some ways that’s a good thing, but advanced pesistent threat (APT) groups are showing more interest than ever and that is troubling. These threat actors have the means to invest in the time and expertise needed to use these techniques to be highly effective at covertly moving information in and out of networks.
Covert movement of data past network boundaries might mean communicating with command and control (C2) servers. It certainly can be used for sneaking malicious payloads into networks. Equally concerning is the prospect of steganography being used to exfiltrate sensitive data without being detected. There’s good reason to believe that this activity is rarely detected too. Let’s take a look at some recent incidents to see how bad actors are using well known techniques to accomplish these things.
Read More
We would be remiss if we did not mention specialized search sites in one of these posts. There are so many websites that index links in a particular industry or links to specific types of documents like patent applications. They don’t fit neatly into other categories but are incredibly useful for people with specific research needs and niche industry players.
There are of course specialized job search websites aplenty, but they’re annoying and chocked full of trackers and their entire goal often seems to be to collect personal information that is specific and current for the sole purpose of resale to data brokers. Same can be said for various shopping comparison and coupon sites. You know who they are already if you care, so we’re just going to move on.
Read More
Smart homes are on the horizon, and we can get a glimpse of things to come by seeing what companies like Google and Amazon are planning and developing. We currently have a variety of connected devices we can buy, but we are just starting to see integrated household systems on the market.
There are convenience benefits to the consumer because this level of monitoring enables new services. When the information is uploaded to Amazon’s cloud based AI service, it can be combined with other data points to provide useful feedback like you forgot to lock the front door, you left the lights on, and so on.
Read More
Searching is one of the core activities people do online. We’ve been posting about it since our introductory post about Google and searching. But in spite of the fact that most people use Google to search there are actually plenty of choices, including some specialized choices. We saw that in our previous post about searching the Internet of Things, and again in the next post when we followed up by discussing a couple viable decentralized search engines.
In this post and in future ones we’ll talk about an area of growing interest in search: Open Source Intelligence (OSINT) These are the tools with which people try to discover information about companies, people, domains, etc. from open source tools that are freely available. Let’s begin with domains and websites.
Read More
In our previous posts we discussed using physical identifiers including facial recognition and other physical characteristics like eyes, fingerprints and veins for authentication and identification. But how does that help providers of online services know who is using the service? The answer might involve behavioral biometrics.
Behavioral biometrics refers to specific behaviors that are tied to individual identities. We tend to exhibit repeating patterns of movement, whether we realize it or not, and react to certain situations in specific, measurable and predictable ways.
Read MoreWelcome back to another installment in our series on steganography. After introducing Digital Steganography Basics, we just finished looking at a modern form of hiding text within text using the snow technique in the post titled Digital Text Based Steganography. Let’s move on to talk about binary files now, as they represent a more popular choice due largely to their substantially larger carrying capacity.
Binary files can obviously be grouped by type: images, audio files, video files, executables, other binary files. For the purposes of steganography however, it’s useful to distinguish between lossy and lossless files. Binary files have a tendency to be large in this age of smartphone videos, and many popular file formats utilize compression to reduce the disk space and bandwidth required to store and transmit them. Lossy file formats find ways to compress the files, losing some portion of the information in the process.
Read More
Google continues to dominate online search, as we outlined in our introductory post about search engines aptly titled Search Engines and Google.
We then dedicated an entire post to decentralized search engines, since your search topics colectively paint a highly detailed view of your personal life. They allow users to run their own nodes. This is great for companies that want to provide internal search to their employees without handing over lots of information to large search providers.
We also explored Internet of Things searching, with search engines like Shodan that allow us to locate everything from webcams to routers to mainframe computers. That’s quite an important topic these days, as vast numbers of devices get connected to the Internet.
In this installment we bring you a look at privacy focused search engines. This category deserves its own post because of the growing importance of online privacy and the central role search providers play.
Read More