Multiverse 2.357
paused to apply patchesWelcome back to another Python programming post. This is a followup to my previous posts about using scapy – that versatile network traffic utility. We went through the basics of creating custom packets, using the basic scapy commands, and then looking at how to build a simple DNS query program using scapy. Feel free to go back and look at those if you missed them – I’m learning as I go, so I tried to be thorough.
In this post we’ll take a quick look at a couple of useful but completely different python utilties called Dshell and Impacket. They’re both unfortunately written for Python2.x, but they are both powerful tools that I’ve recently played around with and they’re worth knowing about. Let’s start with Dshell.
Dshell
Dshell was developed by the US Army Research Labs and it’s a forensic analysis framework, in which plugins can be used. It uses chained decoders to filter different types of network traffic from packet capture (pcap) files. Wow does it ever filter traffic from huge pcap files! The biggest drawback is just that it has aging software requirements. This would be a worthy project to do a python3 refresh on, just saying. The repository is here on github.
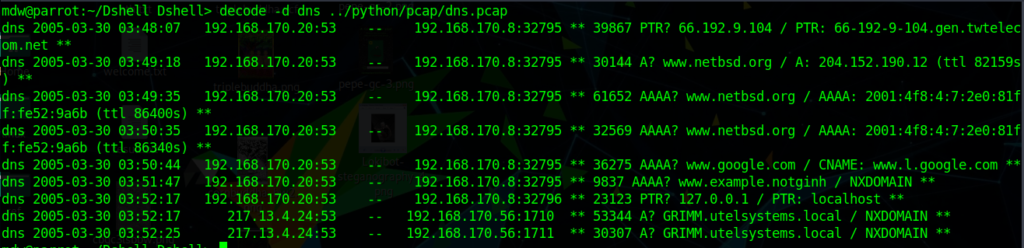
Dshell has decoders that allow you to find traffic from specific protocols like DNS, DHCP, HTTP, even FTP so you can see all that unencrypted activity. It will also filter for traffic from non-standard protocols. Interestingly it has a filter to identify Bitcoin traffic as well, including looking at packets coming and going from all those wacky ports that various mining pools use. It was designed to be extensible as well, so custom filters can be written.
Impacket
Impacket is similar to scapy, but perhaps a bit lower level. Impacket is made for giving programmers access to packet-level data but only for certain protocols. Impacket is for Ethernet only at layer 2, and at layers 3 and 4, impacket supports IP, TCP, UDP, ICMP, IGMP, ARP. There’s pretty good support at higher layers too including authentication via kerberos, NTLM, LDAP. So let’s get started:$ pip install impacket
There are a ton of example scripts on github here: https://github.com/SecureAuthCorp/impacket/tree/master/examples working with all kinds of protocols, MSSQL, Samba, PSExec and much more – it’s well worth checking out. This comes with an Apache license, and more detailed information can be found on the SecureAuth Labs website. A bit of bad news – it only supports Python versions 2.6 and 2.7 at the time of this writing.
I try not to learn Python 2.7 based tools since it’s going to be phased out in a few months, but these two just look so useful that I wanted to tinker a little and try them out. Next time we’ll take a look at another python tool and I don’t think we’ll run out any time soon, so stay tuned!