Multiverse 2.357
paused to apply patches
Interest in steganography is increasing. In some ways that’s a good thing, but advanced pesistent threat (APT) groups are showing more interest than ever and that is troubling. These threat actors have the means to invest in the time and expertise needed to use these techniques to be highly effective at covertly moving information in and out of networks.
Covert movement of data past network boundaries might mean communicating with command and control (C2) servers. It certainly can be used for sneaking malicious payloads into networks. Equally concerning is the prospect of steganography being used to exfiltrate sensitive data without being detected. There’s good reason to believe that this activity is rarely detected too. Let’s take a look at some recent incidents to see how bad actors are using well known techniques to accomplish these things.
We already know from the previous post about LSB steganography that huge amounts of data can be concealed relative to the size of the carrier files in ways that are undetectable to the human eye. We hinted that better techniques would foil our simple analysis tools for detecting even tweaked versions of this method. But in fact even the simple SNOW technique for hiding text in the whitespace in text files is used to great effect. In this post we’re going to take a look at some cases from recent months to see exactly how.
LokiBot found in April to be hiding Zipx file attachments inside PNG images, but TrendMicro reports in August that recently LokiBot has been found to be hiding an encrypted binary inside JPEGs. This binary is extracted, unencrypted and executed by VB Script in order to maintain flexibility – this attacker is continually upgrading the custom software used to steal data.
In this latest round, and there will surely be more since this group is both active and actively developing their malware, the image files used to conceal malicious binaries were real, known images with seemingly random names. This shows the confidence level of the attackers, as a well-known OPSEC rule is to not use images that have been seen before to avoid comparison which could indicate an altered file.
North Korean APT 37 has also been using steganography as part of its ScarCruft malware, mainly targeted at South Korea. They use a multi-stage attack just like in the previous example, with an initial piece of code inside the network calling out to a C2 server to download an image file. This image file that easily makes it through perimeter defenses actually contains an encrypted malicious payload.
According to a Kaspersky post back in May, ScarCruft malware uses a malicious payload that is encrypted and embedded into an image file that has to be decrypted. It is primarily used to exfiltrate data from groups with some interest in North Korea.

PowLoad is a popular malware mostly targeting North American targets, stealing data and using steganography to help accomplish that. Powload malware abuses a publicly available script called (Invoke-PSImage) that helps to Embed malicious scripts in the pixels of a PNG file. Once victims click the document, PowerShell script will be executed and download an image hosted online that contains the malicious code. These attacks were targeted by country.
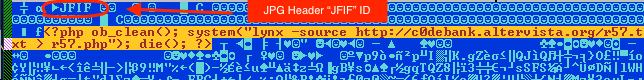
Next up is a report from July about hiding PHP script in JFIF headers – inside a JPEG image. This script simply clears the output buffer then downloads a webshell as text file from the target website and writes it to disk with PHP extension. This PHP code actually lives in the “Comment” EXIF data field and was used to target Brazillian banks. JPEG images typically don’t get scrutinzed by firewalls, but scanning for a “<?php” string in the file headers would’ve caught this.
The ke3chang group, believed to be a Chinese group known as APT15 has been using steganographic techniques to hide data exfiltration according to findings published in July by ESET researchers. Malicious code was hidden in a section of PNG files that is designated to hold compressed text for licensing info. In this case it was simply considered malformed and ignored as it is never considered to be part of the image to be rendered. This is being used to target diplomatic missions.
Researchers at ESET reported in May that they uncovered a Microsoft Exchange backdoor called LightNeuron, that allows the attacker to block or alter email messages, and even compose new ones from legitimate users. it is remotely controlled by commands sent and received using PDF and JPG attachments to embed them. The system appears to be designed for exfiltration of documents, is stealthy and hard to get rid of. Simply deleting the files leaves the victim without a working email server.
This is attributed to the Russian group Turla, and targets are mostly in Eastern Europe and Middle East. The details are fascinating both in how sophisticated this software is and in the level of detail the ESET team has figured out. Disturbing details include the fact that they’ve recently added PDF as a file type, indicating active development. Also it appears there is some capability already in place to make this work against sendmail as well.
One thing to take note of is that we’ve focused exclusively on findings from 2019 in this post. That does not include some important examples from late 2018 like the Ocean Lotus group’s clever use of hiding instructions for malware in PNG files depicting anime characters.
The fact that we have no trouble finding examples of threat actors using steganography to conceal activity or malware should be quite unsettling, especially when you realize that this activity is rarely detected. Image files like JPEG and PNG really don’t get closely inspected the way documents like MS Word and PDF files do. They tend to pass right through network perimeters as email attachments or HTTP requests effortlessly.
Even if there was increased examination of binary files coming and going, would it help? In some examples like the embedded PHP script the malicious code is not even encrypted and it still gets the job done. Consider – how can you scan for encrypted code? When forensics specialists have reason to look they find some of these, but how often is the victim just unaware that anything is wrong? These groups will likely continue to use steganography for a long time to come because it’s way too easy.